New site already getting scanned for attacks
One of the reasons I chose Cloudflare pages over Github pages was that it came with rudimentary analytics. I didn't realize that the free tier came with a level of security analytics as well.
I checked out the analytics expecting myself to be the only person creating any traffic. The analytic data should have contained something like 2 unique visitors, both in the US, both actually me from two different computers/IPs. I was a bit surprised to find that 50% of my traffic came from a single IP in Singapore. Being from Singapore is likely irrelevant, it's just another box that was already part of the bot net trying to recruit a new one. What it scanned was mildly interesting.
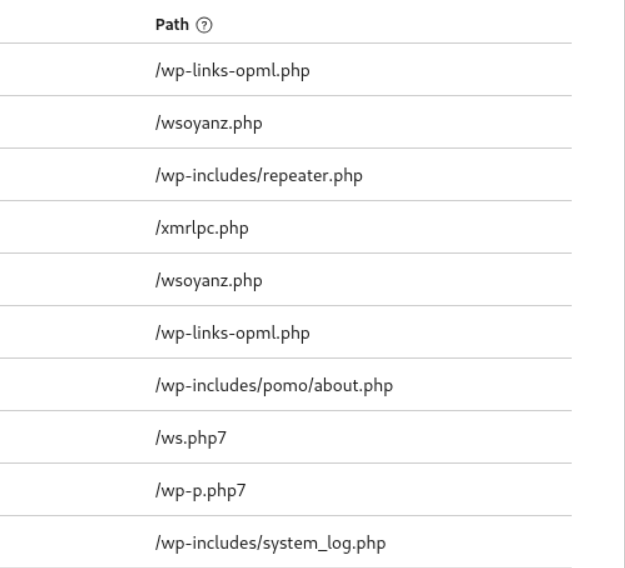
The Cloudflare security analytics are pretty nice especially considering the price (free). You can filter to adaptive sampled requests made by a single IP address. Here are some examples that stood out:
/upgrade.php/xmrlpc.php/cgi-bin/file.php
There were many others that must be very specific vulnerabilities like uchiha.php and minik.php which I couldn't really find a reference to outside of reports of them being scanned. There aren't any public files with those names in GitHub. Most of the rest were all Wordpress related e.g. /wp-admin/wp-login.php.
The IP is owned by 8075 - MICROSOFT-CORP-MSN-AS-BLOCK which seems likely to be somebody's (compromised?) Azure server. I reported that IP with associated logs to Microsoft CERT. I don't expect anything to come of it, but maybe some poor schlub with a vulnerable WP install gets an email and cleans up their site.
While typing this up I looked again and another IP scanned for a lot of paths like /utils/.git/config, /public/.git/config, etc. The fact that someone would have that public on their site is a pretty good signal they're not very experienced or their tools are doing something unexpected. I've never done it, but it appears that you can store your git repository credentials in cleartext via git config credential.helper.
I knew that putting a server up was an invitation to get hacked, but I thought it would require that the site gets some sort of publication or indexing by search engines. Score another point for Hugo or really any static site generation tool. There's no server runtime to hack when the content is statically generated.